Authors:
(1) Daniele Capone, SecSI srl, Napoli, Italy ([email protected]);
(2) Francesco Caturano, Dept. of Electrical Engineering and Information, Technology University of Napoli Federico II, Napoli, Italy ([email protected])
(3) Angelo Delicato, SecSI srl, Napoli, Italy ([email protected]);
(4) Gaetano Perrone, Dept. of Electrical Engineering and Information Technology, University of Napoli Federico II, Napoli, Italy ([email protected])
(5) Simon Pietro Romano, Dept. of Electrical Engineering and Information Technology, University of Napoli Federico II, Napoli, Italy ([email protected]).
Table of Links
III. Dockerized Android: Design
IV. Dockerized Android Architecture
VI. Conclusion and Future Developments, and References
Abstract—The best way to train people about security is through Cyber Ranges, i.e., the virtual platform used by cybersecurity experts to learn new skills and attack vectors. In order to realize such virtual scenarios, container-based virtualization is commonly adopted, as it provides several benefits in terms of performance, resource usage, and portability. Unfortunately, the current generation of Cyber Ranges does not consider mobile devices, which nowadays are ubiquitous in our daily lives. Such devices do often represent the very first entry point for hackers into target networks. It is thus important to make available tools allowing to emulate mobile devices in a safe environment without incurring the risk of causing any damage in the real world. This work aims to propose Dockerized Android, i.e., a framework that addresses the problem of realizing vulnerable environments for mobile devices in the next generation of Cyber Ranges. We show the platform’s design and implementation and show how it is possible to use the implemented features to realize complex virtual mobile kill-chains scenarios.
I. INTRODUCTION
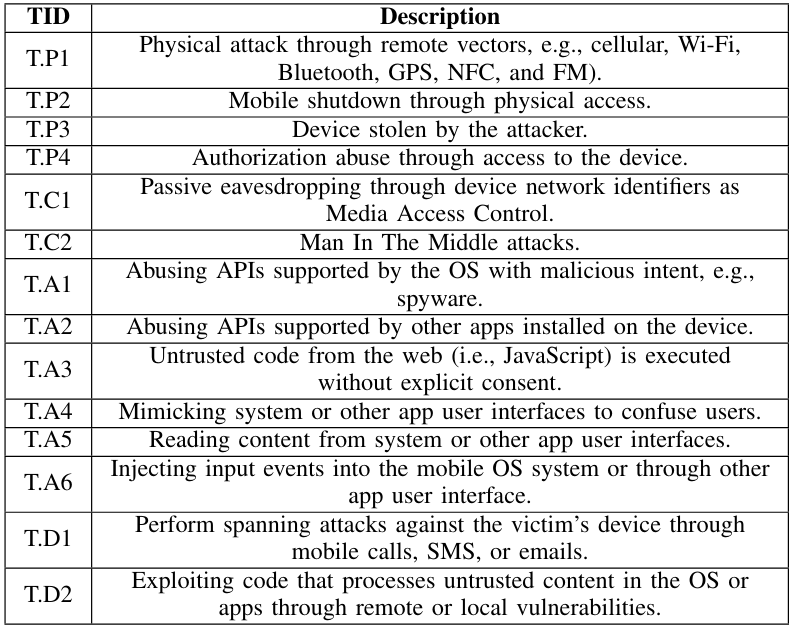
Cyberthreats are real, and they will always be. There will never be 100% secure software. What an organization or a country can do is avoid a security incident from a cyber threat and, if that happens despite all the efforts, minimize the consequences. In order to do so, the organization/country needs highly trained personnel. Currently, one of the most effective ways to train people about security is through Cyber Ranges, i.e., virtual platforms that allow companies and security enthusiasts to learn cyber-security skills in a safe and controlled environment. These platforms can be instrumented for several purposes, even if they are commonly used to create challenges to train security teams. Such challenges are formed by two teams: the “Red Team”, i.e., security experts that help companies to discover vulnerabilities by mimicking a real attacker, and the “Blue Team”, i.e., security experts that try to protect the vulnerable infrastructures from the Red Team. Although it is proven that cyber ranges are essential to improve the effectiveness of security training [1], the problem with current Cyber range generations is that they usually do not consider the existence of mobile devices. This is a strong limitation, as nowadays, mobile devices are commonly adopted by companies and represent a severe security risk. Proofpoint security researchers show that the number of attacks increased by 500% at the beginning of 2022 [2]. A mobile device can browse the Internet, connect to an FTP server, and access all data. Therefore, it could be easily the entrance point for hackers to introduce themselves into the target network. Mayrhofer et al. (2021) [3] provide an Android threat model that covers several mobile threats’ scenarios. The threats summarized in Table I can be physical and/or proximal (P), based on network attacks (N), caused by applications’ abuse (A), or by untrusted data processing.
Therefore, security training for these scenarios is crucial, and cyber-ranges can give a great contribution to such a purpose.
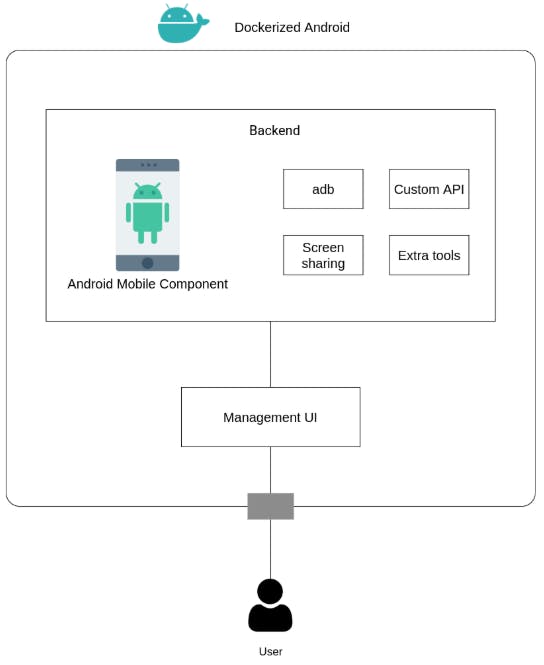
This paper describes the design and implementation of Dockerized Android, i.e., a platform that allows emulating Android devices in a container-based environment that represents a fully realistic yet inherently safe place to study and train.
The paper is organized in six sections. Section II discusses related works associated, respectively, with the introduction of mobile components in Cyber Ranges and the container based emulation of Android devices. Section III proposes a bird’s eye view of the proposed architecture by providing a list of requirements to fulfill, as well as some possible usage scenarios. In Section IV dig deeper into the details associated with its implementation through Docker. Section V provides a qualitative evaluation of what has been done with the help of a few practical usage examples. Finally, Section VI discusses how the proposed architecture naturally lends itself to the study of advanced mobile hacking scenarios like the so
called “mobile cyber kill chain”. It also highlights interesting directions for our future work in the field.
II. RELATED WORKS
Our platform leverages the benefits of container-based virtualization, an approach extensively adopted to create cyber-ranges. Several authors explore the applicability of container-based solutions to the cyber-range domain. Nataka et al. (2020) [4] confirm the performance benefits of using container-based virtualization techniques to reproduce cyber ranges. In another work, Nakata and Otsuka (2020) [5] evaluate the vulnerability coverage of container-based solutions and estimate that 99.3% of vulnerabilities are reproducible. Despite these results, we think that container-based virtualization has several limitations in terms of vulnerability reproduction. This is discussed in detail in [6].
Even though there is rich literature about cyber ranges [7], few researchers have addressed the problem of enhancing them with support for mobile scenarios. One of the most recent works that try to fill this gap is authored by Russo et al. (2020) [8]. The authors give a full overview of the current scenario about both cyber ranges and security training before going into a more detailed description of the work that needs to be done to create Next-Generation Cyber Ranges. The work introduces an attack scenario inspired by Pierini and Trotta (2017) [9] that leverages the so-called “Kerberos Golden Ticket” to obtain administrative privileges. In the proposed scenario, the attacker has no a priori knowledge and time-limited access to the target system. The attacker must proceed through several stages to hack the system, and the last three steps involve the use of mobile techniques. The proposed approach emphasizes the integration tasks needed to build cyber ranges with mobile system support. One of the most significant issues is licensing problems and virtual hardware compatibility. There are indeed several solutions to that problem. Genymotion [10] is a commercial solution that allows the execution of Android virtual devices in three different ways:
• Desktop: allows running Android Virtual Devices on one’s own desktop computer (like the official Android emulator);
• SaaS: allows running Android virtual devices on Genymobile Servers (mostly for test automation);
• PaaS Images: virtual Android images for Cloud providers.
Corellium [11] is yet another commercial solution that allows to run ARM Virtualized Devices in the Cloud. Such a solution provides different features for different use cases, e.g., security research, app streaming, and device modeling. To solve the licensing issues and take advantage of containerbased capabilities, we leverage the official Android Emulation platform [12] to build our mobile cyber-range environment. This choice is justified by the public availability of several solutions allowing to have a Docker Image with a pre-installed Android SDK (and an Emulator as well):
• thyrlian/AndroidSDK: a fully-fledged Android SDK Docker image [13];
• budtmo/docker-android: an ‘Android in Docker’ solution with support for noVNC, as well as video recording capabilities [14];
• bitrise-io/android: a customized Android Docker image [15].
These solutions are based on the SDK and have been realized for development and testing purposes. In particular, they leverage the benefit of container-based virtualization in terms of performance, scalability, and portability but are not able to fully satisfy the security research and Cyber range needs. In particular, these solutions do not offer features that help the realization of scenarios that reproduce the threats described in Table I. However, they are a good starting point to work on for solving the Mobile Virtualization problem.
This paper is available on arxiv under CC by-SA 4.0 Deed (Attribution-Sahrealike 4.0 International license.